It has been a year since President Biden issued the Executive Order on Improving the Nation’s Cybersecurity1 as well as the National Security Memorandum (NSM) 5 on protecting critical infrastructure.2 The Cybersecurity and Infrastructure Agency (CISA) has classified a total of 16 critical infrastructure sectors.3
These are assets, systems, and networks that are so vital to the United States that their incapacitation or destruction would have a debilitating effect on national security, economic security, public health, or safety. Much of this critical infrastructure runs on what is known as Operational Technology (OT).
OT, also referred to as Industrial Control Systems (ICS), is the technology system used to manage and monitor a variety of industrial processes on which our modern lifestyle depends. In the recent past, there was little attention around cybersecurity as it relates to OT. Owners and operators of manufacturing and industrial facilities, outside a few high-value targets such as chemical refineries and nuclear generating stations, expressed little or no concern regarding cyber-related threats and vulnerabilities, and how cyber events could impact critical processes within their facilities.
That mindset is no longer viable in today’s environment because of four major trends:
- Increasing sophistication of OT integration
OT systems were once islands with no connection to the Information Technology (IT) network. In the wake of digital transformation, control systems are now tightly integrated with IT and communication technologies. By adding increased process flexibility, and the monitoring capabilities of modern IT-enabled control technologies, the processes once performed by mechanical relays and stand-alone programmable logic controllers (PLCs) are now online. - Global Internet
Malicious actors and potential saboteurs no longer require physical access to the plant floor to impact operations. Global internet access means threats can now come from afar. - Professionalization of attackers
Cyber attackers such as ransomware gangs are now full-fledged businesses or state-sponsored enterprises. The rise of cryptocurrency has exacerbated the financial incentives for nefarious actors. Attackers frequently share tools, knowledge, and methods that can be used to attack OT networks. - OT-related attacks are already occurring
A recent article explained how threat actors are using password cracking software to take control of PLCs of OT systems.4 The Colonial Pipeline Attack of 2021 and the Oil India Limited Attack in April 2022 are relevant and current examples.5
Difference between IT and OT
Complex factors impact how an enterprise manages and responds to cybersecurity risks. One challenging aspect is that IT, cybersecurity, operations, and engineering personnel all have different viewpoints, experiences, knowledge, and skills. For example, IT network engineers are well-versed in network topologies (e.g., Ethernet6) and conceptual frameworks (e.g., open source interconnect—OSI model7) associated with IT networks. However, OT uses different network topologies (e.g., Modbus8) and frameworks (e.g., Purdue Model9).
All parties involved need to have at least a basic understanding of the common threat actors, vulnerabilities, and attack paths that could impact OT systems. Understanding these differences can assist stakeholders in sharing and understanding the business requirements, technical solutions, and risks to the organization.
Below is a summary of how traditional IT differs from OT systems.
IT
OT
Environment
Typically, business-oriented, and environmentally controlled spaces such as offices, retail, conference halls, and even homes.
Industrial-oriented environments interacting with machines. Resulting in large temperature swings, electro-magnetic noise.
Processing
Various types of data are processed such as: transactions, bulky data, voice, and video. Performs several functions.
Processing includes monitoring, control, and supervisory data. Designed to protect things such as chemical flow rates in water treatment facilities.
Data timing
IT works on transactional processing of data. Latency and refresh rates can vary depending upon business use. Minor delays are typically negligible.
OT works on real-time data processing. Data can become useless in fractions of a second.
Downtime
May have business impacts, but processes supported by IT often have back-up processes available.
Severe operational impacts almost immediately.
Security and safety
Security focuses on confidentiality, integrity, and availability. Access is limited based on privileges of the user.
Safety is the primary concern over security. Access is often only limited by physical controls.
User access
Capable of being supported by robust user authorization and authentication processes.
Many systems have very weak authentication processes.
The air gap myth
There is a common misconception that OT systems are protected by an ‘air gap’—the separation from OT and IT systems. The assumption that this segmentation will solve all cybersecurity risk associated with OT is a myth. Like network segmentation, these air gaps are very effective to mitigate (not eliminate) a cyberattack if implemented correctly. However, a true air gap no longer exists in the interconnected world of Industry 4.0 (digital transformation to interconnectivity and smart grid systems). The practice of depending solely on air gaps and network segmentation for security raises the potential for misunderstanding or underestimating risks.
The CISA.GOV website is an excellent reference for common network architectures and related attack vectors to help shore up access point vulnerabilities.
Here are 5 threats that security cannot mitigate solely by air gaps or network segmentation:
- Dial-up-modem access to remote terminal units (RTU)—Most RTUs require no authentication or password for authentication. It is common to find RTUs with the default passwords still enabled in the field.
- Vendor support—An attacker will attempt to gain access to internal vendor resources or field laptops and piggyback on the connection into the control system local area network.
- Peer utility links—Historically, links from partners or peers have been trusted. In that case, the security of the system is the security of the weakest member. Recently, peer links have been restricted behind firewalls to specific hosts and ports.
- Sending commands directly to data acquisition equipment—The easiest way to control the process is to send commands directly to the data acquisition equipment. Most PLCs, protocol converters, or data acquisition servers lack even basic authentication.
- Communications—Often, it is the responsibility of the corporate IT department to negotiate and maintain long-distance communication lines. However, modern control systems may also integrate direct cellular technologies such as 5G networks. Those 5G networks have unique risks and threat vectors that also need to be assessed.10
Managing the risks
Identifying and managing cybersecurity risks with OT is not a one-time action, but should be a recurring cycle as shown in the figure below:
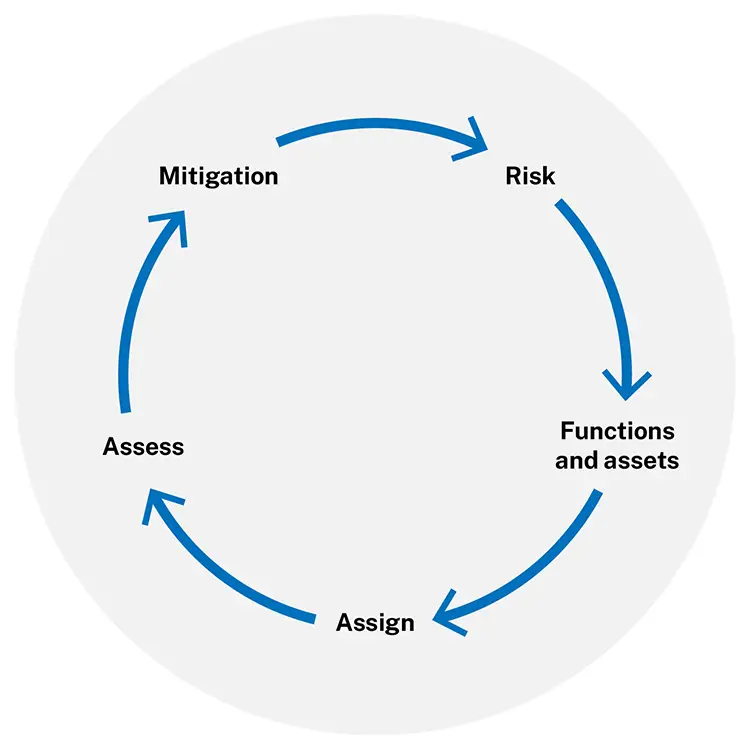
Risk—Recognize that there is legitimate risk with IT and OT systems
Functions and assets—Identify critical functions (or business processes) and the assets that support them
Assign—Assign accountabilities and responsibilities between IT, Operations, Engineering, Procurement, and other departments
Assess—Assess new and existing systems for threats, vulnerabilities, and potential impacts
Mitigate—Implement remediation actions to address risk
As part of the U.S. Department of Energy, the Idaho National Laboratory (INL) has developed the Consequence-driven Cyber-informed Engineering (CCE) process.11 CCE is focused on securing the nation’s critical infrastructure systems. The process begins with the assumption that if skilled and determined adversaries target critical infrastructure systems, they will successfully penetrate the network.
The CCE process is a four-phased approach that incorporates the following baseline assumptions and concepts:
- Assumes the adversary can and will penetrate your defenses
- Breaks the existing trust models—organizations should avoid blind reliance on unverified trust
- Focuses on the worst-case scenarios and real-world impacts
- Works best when engineering, operations, IT, and other departments work together and early in the control system design phase
The National Institute of Standards and Technology (NIST) developed standards and frameworks that can aid organizations in understanding their risks and developing plans to mitigate those risks. Interested individuals can find a wide array of relevant cybersecurity articles and resources on their website.12
Next steps
The Executive Order and NSM 5 are requiring critical infrastructure (including water treatment facilities, power generating facilities, chemical refineries, and other manufacturing organizations) to address the growing risks associated with cyber-enabled sabotage of OT and ICS.
While this article has provided a summary of OT network cybersecurity, an organization should not go it alone. Engaging with a cybersecurity partner helps to assess, address, and mitigate cybersecurity threats.
Complete the form below to meet with a CAI cybersecurity professional and learn about how CAI’s comprehensive cybersecurity solutions take uncertainty out of the equation.
Endnotes
- Biden Jr., Joseph. "Executive Order on Improving the Nation's Cybersecurity." The White House. May 12, 2021, https://bidenwhitehouse.archives.gov/briefing-room/presidential-actions/2021/05/12/executive-order-on-improving-the-nations-cybersecurity/. ↩
- Biden Jr., Joseph. "National Security Memorandum on Improving Cybersecurity for Critical Infrastructure Control Systems." The White House. July 28,2021, https://bidenwhitehouse.archives.gov/briefing-room/statements-releases/2021/07/28/national-security-memorandum-on-improving-cybersecurity-for-critical-infrastructure-control-systems/. ↩
- "Critical Infrastructure Sectors." Cybersecurity and Infrastructure Security Agency. October 21, 2020, https://www.cisa.gov/topics/critical-infrastructure-security-and-resilience/critical-infrastructure-sectors. ↩
- Lakshmanan, Ravie. "Hackers Distributing Password Cracking Tool for PLCs and HMIs to Target Industrial Systems." The Hacker News. July 18, 2022, https://thehackernews.com/2022/07/hackers-distributing-password-cracking.html. ↩
- Musale, Amit. "7 OT Cyber-attacks That Decimated the Critical Infrastructure Businesses." Payatu. June 24, 2022, https://payatu.com/blog/amit.musale/ot-attacks. ↩
- Chai, Wesley, Alissa Irei, and John Burke. "What is Ethernet?" Techtarget.com. October, 2021, https://www.techtarget.com/searchnetworking/definition/Ethernet. ↩
- Shaw, Keith. "The OSI model explained and how to easily remember its 7 layers." Network World. March 14, 2022, https://www.networkworld.com/article/3239677/the-osi-model-explained-and-how-to-easily-remember-its-7-layers.html. ↩
- "Industrial Control System." Trendmicro.com. https://www.trendmicro.com/vinfo/us/security/definition/industrial-control-system. ↩
- Mathezer, Stephen. "Introduction to ICS Security Part 2." SANS Institute. July 16, 2021, https://www.sans.org/blog/introduction-to-ics-security-part-2. ↩
- Ishihara, Yohei. "Private 5G Security Risks in Manufacturing Part 3." Trendmicro.com. October 29, 2021, https://www.trendmicro.com/en_se/research/21/j/security-risks-with-private-5g-Networks-in-manufacturing-part-3.html. ↩
- "Consequence-driven Cyber-informed Engineering." Idaho National Laboratory. https://inl.gov/cce. ↩
- "Cybersecurity Framework." National Institute of Standards and Technology. https://www.nist.gov/cyberframework. ↩